Security in Drupal: what can go wrong?
Benji Fisher
May 27, 2022 - DrupalCamp NJ
Introduction
About me

- Benji Fisher
- @benjifisher on d.o
- @benjifisher on GitHub
- @benjifisher on GitLab
- @benji17fisher on Twitter
Migration subsystem, Usability group, Security team (provisional member)
About Fruition
Build. Grow. Protect.
- Digital Marketing
- Website Design
- Development
- Security & Hosting
Follow along
Find a link to this presentation on my GitLab Pages:
Outline
- Introduction
- What is the OWASP Top Ten?
- What is Drupal?
- A01:2021-Broken Access Control
- A02:2021-Cryptographic Failures
- A03:2021-Injection
- A04:2021-Insecure Design
- A05:2021-Security Misconfiguration
- …
Outline (continued)
- …
- A06:2021-Vulnerable and Outdated Components
- A07:2021-Identification and Authentication Failures
- A08:2021-Software and Data Integrity Failures
- A09:2021-Security Logging and Monitoring Failures
- A10:2021-Server-Side Request Forgery
- Conclusion
Attribution
These slides borrow a lot of text from https://owasp.org/. According to the standard footer,
Unless otherwise specified, all content on the site is Creative Commons Attribution-ShareAlike v4.0 and provided without warranty of service or accuracy.
All of my slide decks have a similar license: see the last slide.
What is the OWASP Top Ten?
Open Web Application Security Project® (OWASP)
The Open Web Application Security Project® (OWASP) is a nonprofit foundation that works to improve the security of software.
source: https://owasp.org/
OWASP is not Drupal-specific. Let’s “get off the island”!
OWASP Top Ten
The OWASP Top 10 is a standard awareness document for developers and web application security. It represents a broad consensus about the most critical security risks to web applications.
source: https://owasp.org/www-project-top-ten/
The list is updated every few years. The most recent version is from 2021.
What is Drupal?
Drupal: a content management system
Drupal is a web-based content management system (CMS):
Enter data in my forms. I will save it to the database, then generate web pages.
Hacker:
Sounds great. Let’s get started!
Drupal: an active, international OSS project
The Drupal community is one of the largest open source communities in the world. We’re more than 1,000,000 passionate developers, designers, trainers, strategists, coordinators, editors, and sponsors working together.
source: https://www.drupal.org/about
Drupal: take security seriously
The security team is an all-volunteer group of individuals who work to improve the security of the Drupal project. Members of the team come from countries across 3 continents … The team was formalized in 2005 with a mailing list and has had 3 team leads in that time period.
A01:2021-Broken Access Control
A02:2021-Cryptographic Failures
A03:2021-Injection
Injection: what goes wrong
- User-supplied data is not validated, filtered, or sanitized by the application.
- Dynamic queries … are used directly in the interpreter.
- Hostile data is used within … search parameters to extract additional, sensitive records.
- Hostile data is directly used or concatenated. …
source: A03:2021 - Injection
Injection: xkcd 327
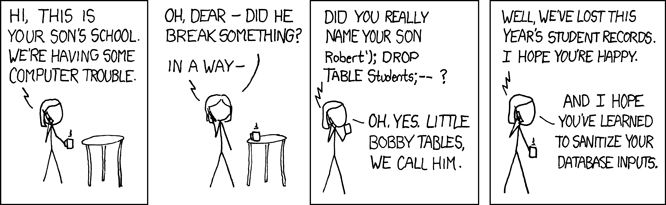
source: https://xkcd.com/327/
Injection in Drupal: SA-CORE-2014-005
Drupal 7 includes a database abstraction API to ensure that queries executed against the database are sanitized to prevent SQL injection attacks.
A vulnerability in this API allows an attacker to send specially crafted requests resulting in arbitrary SQL execution. … this can lead to privilege escalation, arbitrary PHP execution, or other attacks.
This … can be exploited by anonymous users.
source: SA-CORE-2014-005
Injection: my response
Because of the severity of the vulnerability and the simplicity of the update, we tested … and updated the site today.
source: my e-mail to boss and site owner (paraphrase)
Injection: the update
Vulnerable code
Fixed code
(comment snipped from both)
Injection: the next step
// Update the query with the new placeholders.
// preg_replace is necessary to ensure the replacement does not affect
// placeholders that start with the same exact text. For example, if the
// query contains the placeholders :foo and :foobar, and :foo has an
// array of values, using str_replace would affect both placeholders,
// but using the following preg_replace would only affect :foo because
// it is followed by a non-word character.
$query = preg_replace(
'#' . $key . '\b#',
implode(', ', array_keys($new_keys)),
$query
);(line breaks added)
A04:2021-Insecure Design
A05:2021-Security Misconfiguration
A06:2021-Vulnerable and Outdated Components
The best kept secret in web security
The secret:
The most important thing is to do all the boring stuff you already know.
It is a lot like …
Click bait?
How to live a longer, healthier life!
It takes just 4 minutes a day!
Does that seem too good to be true?
Brush your teeth!
- Two minutes, two times a day.
- Best advice you will get today.
- Also floss.
- You really will live a longer, healthier life.
Web security hygiene
- Use good passwords. Have a policy.
- Keep your software up to date.
- Unless hosting is your core business, do not run your own servers.
Drupal: know the schedule
- Security release windows: Wednesdays 12-5 ET
- Drupal core updates (patch versions): third Wednesdays
- Drupal core updates (minor versions): June and December
- Minor versions are supported for one year.
Drupal: know the channels
- Web: Security advisories
- RSS: https://drupal.org/security/rss.xml, https://drupal.org/security/contrib/rss.xml, https://drupal.org/security/psa/rss.xml
- Email: https://www.drupal.org/user (Edit > My newsletters)
- Slack:
#security-questionschannel in Drupal Slack
Unofficial: @drupalsecurity on Twitter (other?)
Drupal: know the difference
- Major version (Drupal 9 to Drupal 10): disruptive
- Minor version (9.3 to 9.4): less disruptive, new features
- Patch version (9.3.6 to 9.3.7): should not be disruptive, bug fixes
- Security release (9.3.7 to 9.3.8): not disruptive (best effort)
Drupal and Symfony
Q: Why is Drupal 9 EOL scheduled for Nov. 2023?
A: Drupal 9 uses Symfony 4, which is EOL in Nov. 2023.
A07:2021-Identification and Authentication Failures
A08:2021-Software and Data Integrity Failures
A09:2021-Security Logging and Monitoring Failures
A10:2021-Server-Side Request Forgery
Conclusion
Summary
- Introduction
- What is the OWASP Top Ten?
- What is Drupal?
- A01:2021-Broken Access Control
- A02:2021-Cryptographic Failures
- A03:2021-Injection
- A04:2021-Insecure Design
- A05:2021-Security Misconfiguration
- …
Summary (continued)
- …
- A06:2021-Vulnerable and Outdated Components
- A07:2021-Identification and Authentication Failures
- A08:2021-Software and Data Integrity Failures
- A09:2021-Security Logging and Monitoring Failures
- A10:2021-Server-Side Request Forgery
- Conclusion
References
Questions
Copyleft

This slide deck by
Benji
Fisher is licensed under a
Creative
Commons Attribution-ShareAlike 4.0 International License.
Based on a work at
https://gitlab.com/benjifisher/slide-decks.